Authentication Types
Everbridge REST APIs can support the following authentications:
OAUth 2.0 Authentication
To call Everbridge REST endpoints using OAuth 2.0 authentication, the client first needs to call the token API endpoint to get an Id Token. Each subsequent request is sent using Id token as a bearer token in the header.
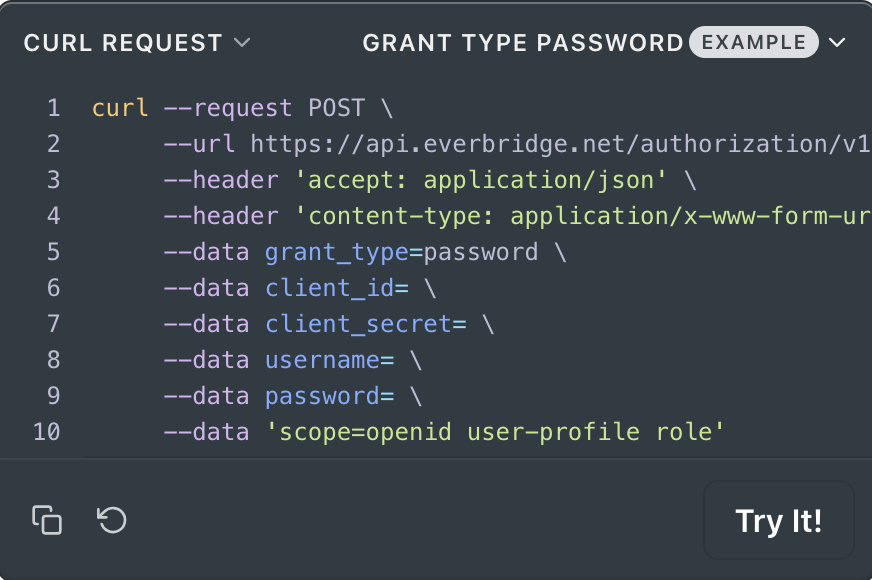
In the request form body, you should include:
- grant_type = “password”
- client_id
- client_secret
- username
- password
- scope = "openid user-profile role"
Where
- The Client ID and Client Secret would be obtained from the Everbridge Manager Portal self-service workflow.
- Username and Password must be created by following this guide
Once a valid ID token is returned, you must submit the token as a "Bearer" token in the header of all subsequent requests to the Everbridge APIs.
- For password grant type the "id_token" is required.
Copy id_token [NOT access_token]
Use the copy icon to quickly copy Bearer <id_token> to your clipboard
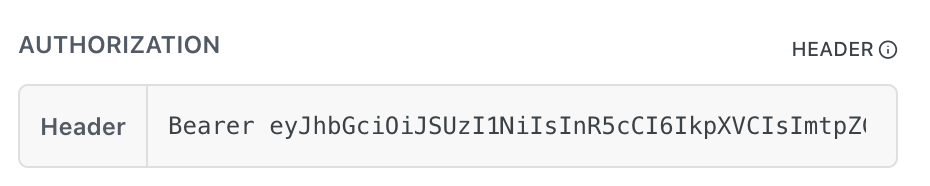
- Paste the Token in the "Header" value from the Authorization drop down selection.
- The token is valid for 28800 seconds, which is 8 hours
User with multiple roles
If the user in Everbridge Suite has multiple roles, or the user is account admin, and you want to use specific role to access the endpoint, you can specify the roleId the request example below. In this way, the system will create an ID Token to include this Role ID.
When using an Account Admin user, the Role ID sent with the request should be for the Org Admin role, not the Account Admin role.
curl --request POST \
--url https://api.everbridge.net/authorization/v1/tokens \
--header 'accept: application/json' \
--header 'content-type: application/x-www-form-urlencoded' \
--header 'roleId: 3074242338834534' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'client_id=sample_integration_client_id' \
--data-urlencode 'client_secret=*******************' \
--data-urlencode 'username=sample_integration_api_user' \
--data-urlencode 'password=****************' \
--data-urlencode 'scope=openid user-profile role'
The username and password pair must belong to a user who has the API User role within an organization that has been granted access to the API product. These privileges can only currently be set by direct DB access; they are not available through the EBAdmin portal at this time.
Further, each API method has its own permissions, so a user can be enabled to use the API but only granted access to a subset of the API methods. This gives you fine-grained control of how users access the information for your organization.
Basic Authentication
The EB Suite REST API uses Basic Authentication over HTTPs. Standard HTTP Authorization header is used to pass Basic authentication information.
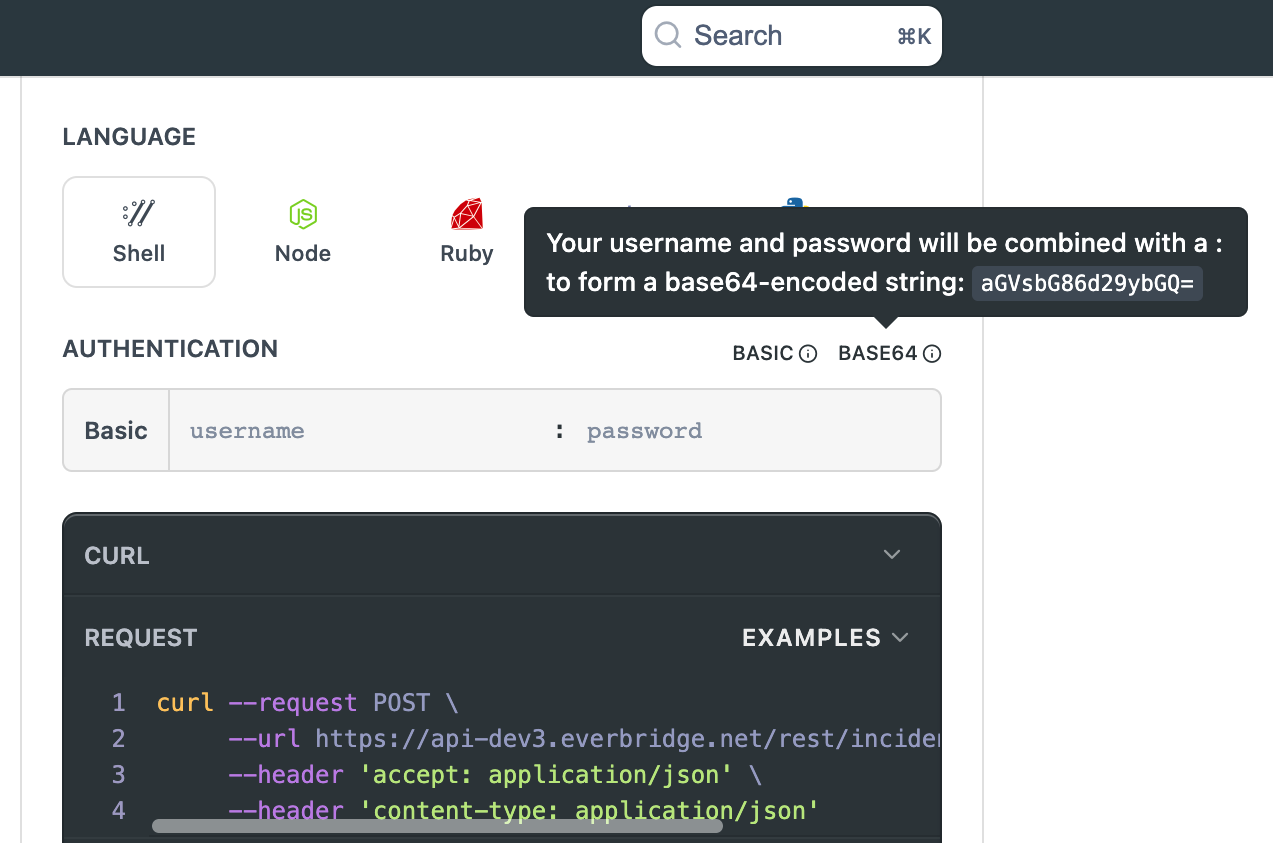
The value of this header should be a Base64 encoding of username and password of your API user in the format of <username:password>. For example, if API user credentials were username "ryan" and password "thisisabadpassword", then the credentials field in the would be the Base64 encoding of ryan:thisisabadpassword, or cnlhbjp0aGlzaXNhYmFkcGFzc3dvcmQ=.
Authorization: Basic cnlhbjp0aGlzaXNhYmFkcGFzc3dvcmQ=
When using this online portal (Readme), just pass in the API user credentials in the username/password fields and the tool will create the base64 encode credentials.
Access Token Authentication
Access Token is a legacy authentication method. If your organization requires this functionality please see our support KB article on how to enable and authenticate using this authentication type.
Examples and live requests of all supported authentication use cases can be found in our API documentation page for OAuth Authentication.
Updated 12 days ago

